- Intercepted HTTP/HTTPS Request Processing
- Policy Types
- Policy Order
- Creating a Policy
- Adding and Editing Secure Group Tags for a Policy
- Adding Routing Destination and IP Spoofing Profile to Routing Policy
- Access Policies: Blocking Objects
- Archive Inspection Settings
- About Client Applications
- Using Client Applications in Policies
- Defining Policy Membership Using Client Applications
- Defining Policy Control Settings Using Client Applications
- Time Ranges for Policies and Acceptable Use Controls
- Creating a Time Range
- Volume Quota Calculations
- Time Quota Calculations
- Defining Time and Volume Quotas
- Using URL Categories to Identify Web Requests
- Using URL Categories to Action Web Request
- About Remote Users
- How to Configure Identification of Remote Users
- Configuring Identification of Remote Users
Create Policies to Control Internet Requests
This topic contains the following sections:
Overview of Policies: Control Intercepted Internet Requests
When the user creates a web request the configured Web Security Appliance intercepts the requests and manages the process of which the request travels to get to its final outcome, be that accessing a particular web site, an email or even accessing an online application. In configuring the Web Security Appliance policies are created to define the criteria and actions of requests made by the user.
Policies are the means by which the Web Security Appliance identifies and controls web requests. When a client sends a web request to a server, the Web Proxy receives the request, evaluates it, and determines to which policy it belongs. Actions defined in the policy are then applied to the request.
The Web Security Appliance uses multiple policy types to manage different aspects of web requests. Policy types might fully manage transactions by themselves or pass transactions along to other policy types for additional processing. Policy types can be groups by the functions they perform, such as access, routing, or security.
AsyncOS evaluates transactions based on policies before it evaluates external dependencies to avoid unnecessary external communication from the appliance. For example, if a transaction is blocked based on a policy that blocks uncategorized URLs, the transaction will not fail based on a DNS error.
Intercepted HTTP/HTTPS Request Processing
The following diagram depicts the flow of an intercepted Web request as it is processed by the appliance.
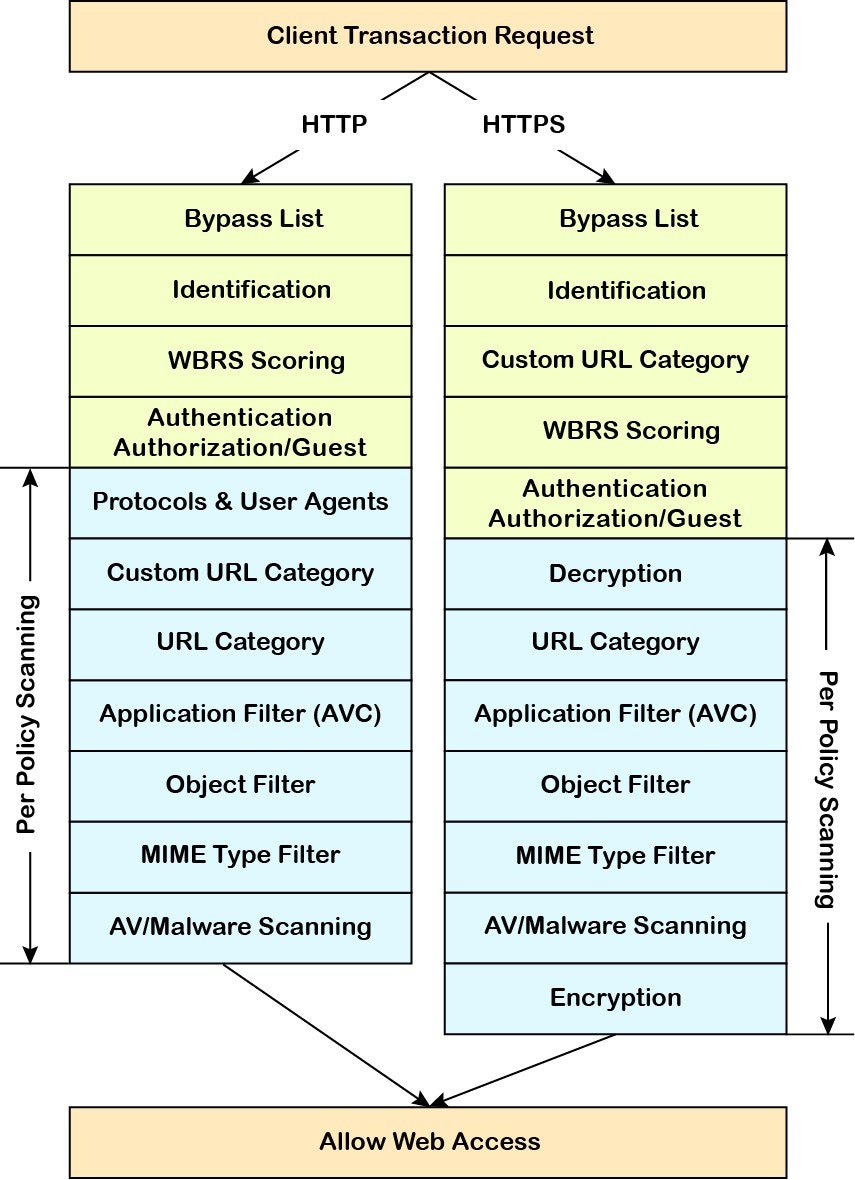
Also see the following diagrams depicting various transaction processing flows:
- Identification Profiles and Authentication Processing – No Surrogates and IP-based Surrogates
- Identification Profiles and Authentication Processing – Cookie-based Surrogates
- Policy Group Transaction Flow for Access Policies
- Policy Group Transaction Flow for Decryption Policies
- Controlling HTTPS Traffic
Managing Web Requests Through Policies Task Overview
Task List for Managing Web Requests through Policies
Links to Related Topics and Procedures
Set up and sequence Authentication Realms
(For upstream proxies) Create a proxy group.
(Optional) Create Custom Client Applications
(Optional) Create Custom URL Categories
Create Identification Profiles
(Optional) Create time ranges to Limit Access by Time of Day
Create and Order Policies
Managing Web Requests Through Policies Best Practices
If you want to use Active Directory user objects to manage web requests, do not use primary groups as criteria. Active Directory user objects do not contain the primary group.
Policies
- Policy Types
- Policy Order
- Creating a Policy
Policy Types
Block, allow or redirect inbound HTTP, FTP, and decrypted HTTPS traffic.
Access policies also manage inbound encrypted HTTPS traffic if the HTTPS proxy is disabled.
Allow or block SOCKS communication requests.
Allow or deny access to a Software as a Service (SaaS) application.
Use single sign-on to authenticate users and increase security by allowing access to applications to be quickly disabled.
To use the single sign-on feature of policies you must configure the Web Security Appliance as an identity provider and upload or generate a certificate and key for SaaS.
Encrypted HTTPS Management
Decrypt, pass through, or drop HTTPS connections.
AsyncOS passes decrypted traffic to Access policies for further processing.
Manage data uploads to the web. Data Security policies scan outbound traffic to ensure it complies to company rules for data uploads, based on its destination and content. Unlike External DLP policies, which redirect outbound traffic to external servers for scanning, Data Security policies use the Web Security Appliance to scan and evaluate traffic.
External DLP (Data Loss Prevention)
Send outbound traffic to servers running 3rd-party DLP systems, which scan it for adherence to company rules for data uploads. Unlike Data Security policies, which also manage data uploads, External DLP policies move scanning work away from the Web Security Appliance , which frees resources on the appliance and leverages any additional functionality offered by 3rd-party software.
Outbound Malware Scanning
Block, monitor, or allow requests to upload data that may contain malicious data.
Prevent malware that is already present on your network from being transmitted to external networks.
Direct web traffic through upstream proxies or direct it to destination servers. You might want to redirect traffic through upstream proxies to preserve your existing network design, to off-load processing from the Web Security Appliance , or to leverage additional functionality provided by 3rd-party proxy systems.
If multiple upstream proxies are available, the Web Security Appliance can use load balancing techniques to distribute data to them.
Retian the client's source IP address, change it to the web proxy IP, or a custom IP using IP Spooing profile.
Each policy type uses a policy table to store and manage its policies. Each policy table comes with a predefined, global policy, which maintains default actions for a policy type. Additional, user-defined policies are created and added to the policy table as required. Policies are processed in the order in which they are listed in the policy table.
Individual policies define the user-request types they manage, and the actions they perform on those requests. Each policy definition has two main sections:
- Identification Profiles and Users – Identification Profiles are used in policy membership criteria and are particularly important as they contain many options for identifying web transaction. They also share many properties with policies.
- Advanced – The criteria used to identify users to which the policy applies. One or more criteria can be specified in a policy, and all must be match for the criteria to be met.
- Protocols – Allow the transfer of data between various networking devices such as http, https, ftp, etc.
- Proxy Ports – the numbered port by which the request accesses the web proxy,
- Subnets – The logical grouping of connected network devices (such as geographic location or Local Area Network [LAN]), where the request originated
- Time Range – Time ranges can be created for use in policies to identify or apply actions to web requests based on the time or day the requests were made. The time ranges are created as individual units.
- URL Categories – URL categories are predefined or custom categories of websites, such as News, Business, Social Media, etc. These can be used to identify or apply actions to web requests.
- User Agents – These are the client applications (such as updaters and Web browsers) used to make requests. You can define policy criteria based on user agents, and you can specify control settings based on user agents. You can also exempt user agents from authentication, which is useful for applications that cannot prompt for credentials. You can define custom user agents but cannot re-use these definitions other policies.
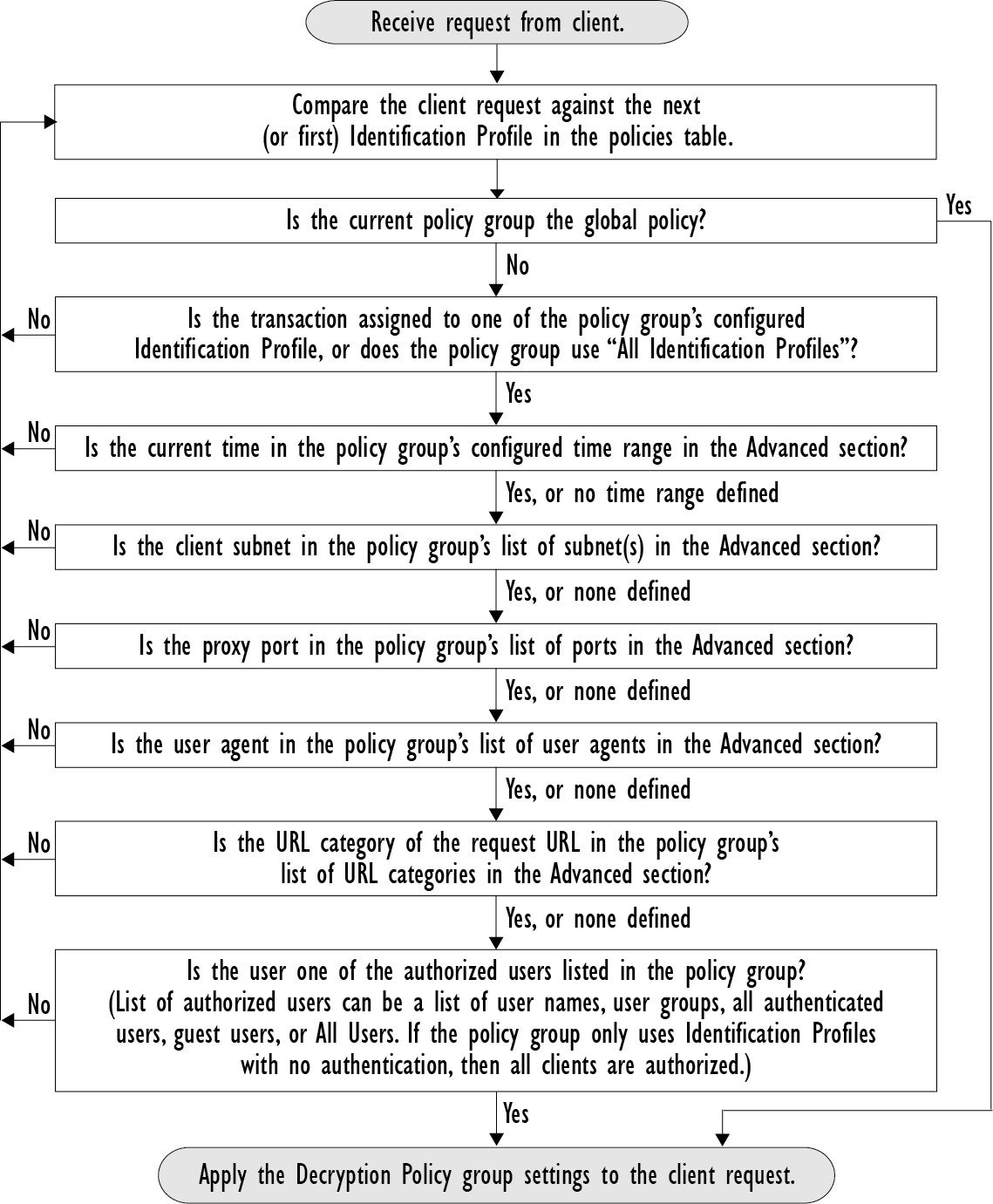
Policy Order
The order in which policies are listed in a policy table determines the priority with which they are applied to Web requests. Web requests are checked against policies beginning at the top of the table and ending at the first policy matched. Any policies below that point in the table are not processed.
If no user-defined policy is matched against a Web request, then the global policy for that policy type is applied. Global policies are always positioned last in Policy tables and cannot be re-ordered.
The following diagram depicts the flow of a client request through the Access policies table.
Creating a Policy
Before you begin
- Enable the appropriate proxy:
- Web Proxy (for HTTP, decrypted HTTPS, and FTP)
- HTTPS Proxy
- SOCKS Proxy
Procedure
In the Policy Settings section, use the Enable Identity check box to enable this policy, or to quickly disable it without deleting it.
Assign a unique policy Name .
A Description is optional.
From the Insert Above drop-down list, choose where this policy is to appear in the table.
In the Policy Expires area, check the Set Expiration for Policy check box to set the expiry time for the policy. Enter the date and time for the policy expiration that you want to set. The policies are automatically disabled once they exceed the set expiry time.
System checks the policies every minute to disable the policies which get expired during the minute. For example, if a policy is set to expire at 11:00, at maximum it will be disabled by 11:01.
You will receive an email prior to three days of the policy expiry and another one upon policy expiry.
You can set the policy expiration time through Cisco Content Security Management Appliances as well. The policies will get expired after the set expiry time but will not be shown as disabled in the Cisco Content Security Management Appliances GUI.
Once you set the policy expiration feature, the expiry happens based on the appliance's local time settings.
In the Policy Member Definition section, specify how user and group membership is defined: from the Identification Profiles and Users list, choose one of the following:
- All Identification Profiles – This policy will apply to all existing profiles. You must also define at least one Advanced option.
- Select One or More Identification Profiles – A table for specifying individual Identification Profiles appears, one profile-membership definition per row.
If you chose All Identification Profile s:
- Specify the authorized users and groups to which this policy applies by selecting one of the following options:
- All Authenticated Users – All users identified through authentication or transparent identification.
- Selected Groups and Users – Specified users and groups are used. To add or edit the specified ISE Secure Group Tags (SGTs) and the specified Users, click the link following the appropriate label. For example, click the list of currently specified users to edit that list. See Adding and Editing Secure Group Tags for a Policy for more information. If you use ISE, you can add or edit ISE Secure Group Tags. This is not supported in ISE-PIC deployments. To add or edit the specified ISE Groups, click the link following the label. This option is specific to ISE-PIC.
- Guests – Users connected as guests and those failing authentication.
- All Users – All clients, whether authenticated or not. If this option is selected, at least one Advanced option also must be provided.
If you chose Select One or More Identification Profiles , a profile-selection table appears.
- Choose an Identification Profile from the Select Identification Profile drop-down list in the Identification Profiles column.
- Specify the Authorized Users and Groups to which this policy applies:
- All Authenticated Users – All users identified through authentication or transparent identification.
- Selected Groups and Users – Specified users and groups are used. To add or edit the specified ISE Secure Group Tags (SGTs) and the specified Users, click the link following the appropriate label. For example, click the list of currently specified users to edit that list. See Adding and Editing Secure Group Tags for a Policy for more information.
- Guests – Users connected as guests and those failing authentication.
- To add a row to the profile-selection table, click Add Identification Profile . To delete a row, click the trash-can icon in that row.
Repeat steps (a) through (c) as necessary to add all desired Identification Profiles.
Expand the Advanced section to define additional group membership criteria. (This step may be optional depending on selection in the Policy Member Definition section. Also, some of the following options will not be available, depending on the type of policy you are configuring.) .
Select the protocols to which this policy will apply. All others means any protocol not selected. If the associated identification profile applies to specific protocols, this policy applies to those same protocols
Applies this policy only to traffic using specific ports to access the web proxy. Enter one or more port numbers, separating multiple ports with commas.
For explicit forward connections, this is the port configured in the browser.
For transparent connections, this is the same as the destination port.
Applies this policy only to traffic on specific subnets. Select Specify subnets and enter the specific subnets, separated by commas.
Leave Use subnets from selected Identities selected if you do not want additional filtering by subnet.
You can apply time ranges for policy membership:
- Time Range – Choose a previously defined time range (Time Ranges and Quotas).
- Match Time Range – Use this option to indicate whether this time range is inclusive or exclusive. In other words, whether to match only during the range specified, or at all times except those in the specified range.
You can restrict policy membership by specific destinations (URLs) and by categories of URLs. Select all desired custom and predefined categories. See Creating and Editing Custom URL Categories for information about custom categories.
You can select specific user agents, and define custom agents using regular expressions, as part of membership definition for this policy.
- Common User Agents
- Browsers – Expand this section to select various Web browsers.
- Others – Expand this section to select specific non-browser agents such as application updaters.
Adding and Editing Secure Group Tags for a Policy
To change the list of Secure Group Tags (SGTs) assigned to a particular Identification Profile in a policy, click the link following the ISE Secure Group Tags label in the Selected Groups and Users list on the Add/Edit Policy page. (See Creating a Policy.) This link is either “No tags entered,” or it is a list of currently assigned tags. The link opens the Add/Edit Secure Group Tags page.
All SGTs currently assigned to this policy are listed in the Authorized Secure Group Tags section. All SGTs available from the connected ISE server are listed in the Secure Group Tag Search section.
Procedure
To add one or more SGTs to the Authorized Secure Group Tags list, select the desired entries in the Secure Group Tag Search section, and then click Add .
- The SGTs already added, are highlighted in green. To quickly find a specific SGT in the list of those available, enter a text string in the Search field.
- When a Web Security Appliance is connected to ISE/ISE-PIC, default SGTs from ISE/ISE-PIC are also displayed. These SGTs will not have users assigned. Ensure that you select the correct SGTs.
To remove one or more SGTs from the Authorized Secure Group Tags list, select those entries and then click Delete .
Click Done to return to the Add/Edit Group page.
What to do next
Related Topics
- Time Ranges and Quotas
- Using Client Applications in Policies
Adding Routing Destination and IP Spoofing Profile to Routing Policy
You can configure how the web proxy forwards the web traffic and the requests the source IP address by configuring the routing destination and IP spoofing profile in routing policies.
- The global routing policy is enabled by default even if an upstream proxy group is not configured on the appliance.
- IP spoofing profiles are not related to routing destination, and can be configured independently.
- Routing Policy can be enabled without configuring an upstream proxy.
To configure an upstream proxy group for a routing policy in Security Management appliance, save the configuration file of the Web Security Appliance and import it on the Security Management appliance. Otherwise, the Security Management appliance shows the upstream proxy as "Not Found" and the routing policy will be disabled after the config push.
Procedure
Choose Web Security Manager > Routing Policies.
On the Routing Policies page, click the link under Routing Destination column for the routing policy that you want to configure the upstream proxy group.
Choose an appropriate upstream proxy group for the selected policy from the following:
Use Global Policy Settings
The web proxy uses the settings defined in the Global Policy. This is the default action for user defined policy groups. By default, the routing destination for Global Routing Policy is set as Direct Connection.
Applies to user defined policy groups only.
The web proxy forwards web traffic directly to its destination web server.
Custom upstream proxy group
The web proxy redirects the web traffic to an external upstream proxy group. For more information about creating upstream proxy groups, see Upstream Proxies.
On the Routing Policies page, click the link under IP Spoofing column for the routing policy that you want to configure the IP spofing profile.
Choose an appropriate IP spoofing profile for the selected policy from the following:
Use Global Policy Settings
The web proxy uses the settings defined in the Global Policy. This is the default action for user defined policy groups. By default, the IP spoofing is disabled for the Global Routing Policy.
Applies to user defined policy groups only.
Do No Use IP Spoofing
The web proxy changes the request source IP address to match its own address to increase security.
The web proxy retains the source address so that it appears to originate from the source client rather than from the Web Security Appliance .
Custom spoofing profile name
The web proxy changes the request source IP address to custom IP defined in the selected custom IP spoofing profile name.
Submit and Commit your changes.
What to do next
Related Topics
- Upstream Proxies
- Web Proxy IP Spoofing
Policy Configuration
Each row in a table of policies represents a policy definition, and each column displays current contains a link to a configuration page for that element of the policy.
Protocols and User Agents
Used to control policy access to protocols and configure blocking for particular client applications, such as instant messaging clients, web browsers, and Internet phone services. You can also configure the appliance to tunnel HTTP CONNECT requests on specific ports. With tunneling enabled, the appliance passes HTTP traffic through specified ports without evaluating it.
AsyncOS for Web allows you to configure how the appliance handles a transaction based on the URL category of a particular HTTP or HTTPS request. Using a predefined category list, you can choose to block, monitor, warn, or set quota-based or time-based filters.
You can also create custom URL categories and then choose to block, redirect, allow, monitor, warn, or apply quota-based or time-based filters for Websites in the custom categories. See Creating and Editing Custom URL Categories for information about creating custom URL categories.
In addition, you can add exceptions to blocking of embedded or referred content.
The Application Visibility and Control engine (AVC) engine is an Acceptable Use policy component that inspects Web traffic to gain deeper understanding and control of Web traffic used for applications. The appliance allows the Web Proxy to be configured to block or allow applications by Application Types, and by individual applications. You can also apply controls to particular application behaviors, such as file transfers, within a particular application. See Managing Access to Web Applications for configuration information.
These options let you configure the Web Proxy to block file downloads based on file characteristics, such as file size , file type , and MIME type . An object is, generally, any item that can be individually selected, uploaded, downloaded and manipulated . See Access Policies: Blocking Objects for information about specifying blocked objects.
Anti-Malware and Reputation
Web reputation filters allow for a web-based reputation score to be assigned to a URL to determine the probability of it containing URL-based malware. Anti-malware scanning identifies and stops web-based malware threats. Advanced Malware Protection identifies malware in downloaded files.
The Anti-Malware and Reputation policy inherits global settings respective to each component. Within Security Services > Anti-Malware and Reputation , malware categories can be customized to monitor or block based on malware scanning verdicts and web reputation score thresholds can be customized. Malware categories can be further customized within a policy. There are also global settings for file reputation and analysis services.
HTTP ReWrite Profile
You can configure custom header profiles for HTTP requests and can create multiple headers under a header rewrite profile. The header rewrite profile feature enables the appliance to pass the user and group information to another upstream device after successful authentication. The upstream proxy considers the user as authenticated, bypasses further authentication, and provides access to the user based on the defined access policies.
Deletes the created policy.
Access Policies: Blocking Objects
You can use the options on the Access Policies: Objects page to block file downloads based on file characteristics, such as file size, file type, and MIME type. An object is, generally, any item that can be individually selected, uploaded, downloaded and manipulated.
You can specify a number of types of objects to be blocked by each individual Access policy, and by the Global policy. These object types include Archives, Document Types, Executable Code, Web Page Content, and so on.
Procedure
On the Access Policies page ( Web Security Manager > Access Policies ), click the link in the Objects column of the row representing the policy you wish to edit.
Choose the desired type of object blocking for this Access policy:
- Use Global Policy Objects Blocking Settings – This policy uses the object-blocking settings defined for the Global Policy; these settings are displayed in read-only mode. Edit the settings for the Global Policy to change them.
- Define Custom Objects Blocking Settings – You can edit all object-blocking settings for this policy.
- Disable Object Blocking for this Policy – Object blocking is disabled for this policy; no object-blocking options are presented.
If you chose Define Custom Objects Blocking Settings in the previous step, select and deselect object-blocking options on the Access Policies: Objects page as needed.
Object Size
You can block objects based on their download size:
- HTTP/HTTPS Max Download Size – Either provide the maximum object size for HTTP/HTTPS download (objects larger than this will be blocked), or indicate that there is no maximum size for object download via HTTP/HTTPS.
- FTP Max Download Size – Either provide the maximum object size for FTP download (objects larger than this will be blocked), or indicate that there is no maximum size for object download via FTP.
Block Object Type
Expand this section to select types of Archive files that are to be blocked. This list includes Archive types such as ARC, BinHex, and StuffIt.
Expand this section to select whether to Allow , Block , or Inspect specific types of Inspectable Archive files. Inspectable Archives are archive or compressed files that the Web Security Appliance can inflate to inspect each of the contained files in order to apply the file-type block policy. The Inspectable Archives list includes archive types such as 7zip, Microsoft CAB, RAR, and TAR.
The following points apply to archive inspection:
- Only archive types marked Inspect will be inflated and inspected.
- Only one archive will be inspected at a time, Additional concurrent inspectable archives may not be inspected.
- If an inspected archive contains a file type that is assigned the Block action by the current policy, the entire archive will be blocked, regardless of any allowed file types it may contain.
- An inspected archive that contains an unsupported archive type will be marked as “unscannable.” If it contains a blocked archive type, it will be blocked.
- Password-protected and encrypted archives are not supported and will be marked as “unscannable.”
- An inspectable archive which is incomplete or corrupt is marked as “unscannable.”
- The DVS Engine Object Scanning Limits value specified for the Anti-Malware and Reputation global settings also applies to the size of an inspectable archive; an object exceeding this size is marked as “unscannable.” See Enabling Anti-Malware and Reputation Filters for information about this object size limit.
- An inspectable archive marked as “unscannable” can be either Blocked in its entirety or Allowed in its entirety.
- When access policies are configured to block custom MIME types, and archive inspection is enabled:
- If the appliance directly downloads a file with the custom MIME type as part of the content-type header, access is blocked.
- If the same file is part of a ZIP/archive file, the appliance inspects the archive and determines the MIME type based on its own MIME evaluation. If the MIME evaluated by the appliance's engine does not match the configured custom MIME type, the content is not blocked.
See Archive Inspection Settings for information about configuring archive inspection.
Expand this section to select types of text documents to be blocked. This list includes document types such as FrameMaker, Microsoft Office, and PDF.
Expand this section to select types of executable code to be blocked. The list includes Java Applet, UNIX Executable and Windows Executable.
Types of installers to be blocked; the list includes UNIX/LINUX Packages.
Types of media files to be blocked. The list includes Audio, Video and Photographic Image Processing Formats (TIFF/PSD).
This list includes BitTorrent Links ( .torrent ).
Web Page Content
This list includes Flash and Images.
This list includes Calendar Data.
Custom MIME Types
You can define additional objects/files to be blocked based on MIME type.
Enter one or more MIME types in the Block Custom MIME Types field, one per line.
Archive Inspection Settings
You can Allow, Block, or Inspect specific types of Inspectable Archives for individual Access policies. Inspectable Archives are archive or compressed files that the Web Security Appliance can inflate to inspect each of the contained files in order to apply the file-type block policy. See Access Policies: Blocking Objects for more information about configuring archive inspection for individual Access policies.
During archive inspection, nested objects are written to disk for examination. The amount of disk space that can be occupied at any given time during file inspection is 1 GB. Any archive file exceeding this maximum disk-use size will be marked unscannable.
The Web Security Appliance ’s Acceptable Use Controls page provides system-wide Inspectable Archives Settings; that is, these settings apply to archive extraction and inspection whenever enabled in an Access policy.
Procedure
Choose Security Services > Acceptable Use Controls .
Click the Edit Archives Settings button.
Edit the Inspectable Archives Settings as needed.
- Maximum Encapsulated Archive Extractions – Maximum number of “encapsulated” archives to be extracted and inspected. That is, maximum depth to inspect an archive containing other inspectable archives. An encapsulated archive is one that is contained in another archive file. This value can be zero through five; depth count begins at one with the first nested file. The external archive is considered file zero. If the archive has files nested beyond this maximum nested value, the archive is marked as unscannable. Note that this will impact performance.
- Block Uninspectable Archives – If checked, the Web Security Appliance will block archives it failed to inflate and inspect.
Submit and Commit Changes .
Block, Allow, or Redirect Transaction Requests
The web proxy controls web traffic based on the policies that you create for groups of transaction requests.
- Allow. The Web Proxy permits the connection without interruption. Allowed connections may not have been scanned by the DVS engine.
- Block. The Web Proxy does not permit the connection and instead displays an end user notification page explaining the reason for the block.
- Redirect. The Web Proxy does not allow the connection to the originally requested destination server and instead connects to a different specified URL, see Redirecting Traffic in the Access Policies.
Generally, different types of policies control traffic based on the transport protocol.